leads4pass 350-701 dumps consist of 598 up-to-date exam questions and answers specifically designed for the Implementing and Operating Cisco Security Core Technologies (SCOR) exam.
leads4pass 350-701 dumps are accompanied by lightweight PDF and VCE tools, which enhance the learning experience and facilitate candidates in their preparation.
Visit the latest 350-701 dumps: https://www.leads4pass.com/350-701.html. Guaranteed a 100% pass rate on the CCNP Security Core Certification exam with the included 598 up-to-date exam questions and answers.
Practice some 350-701 dumps exam questions online
| From | Number of exam questions | Last updated | Exam name |
| leads4pass | 15 | 350-701 dumps | Implementing and Operating Cisco Security Core Technologies (SCOR) |
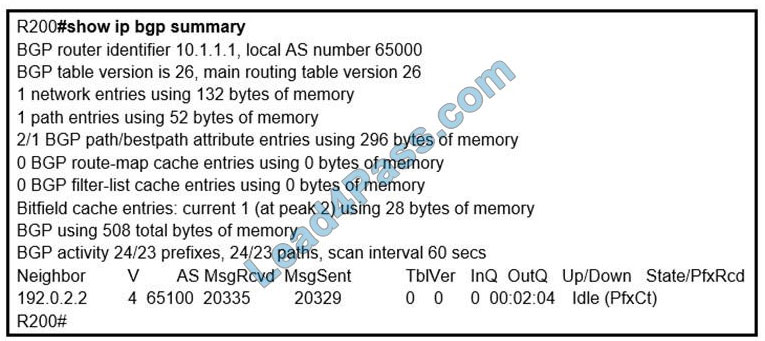
Question 1:
Under which two circumstances is a CoA issued? (Choose two)
A. A new authentication rule was added to the policy on the Policy Service node.
B. An endpoint is deleted on the Identity Service Engine server.
C. C. A new Identity Source Sequence is created and referenced in the authentication policy.
D. An endpoint is profiled for the first time.
E. A new Identity Service Engine server is added to the deployment with the Administration persona
Correct Answer: BD
Does the profiling service issue the change of authorization in the following cases:?Endpoint deleted–When an endpoint is deleted from the Endpoints page and the endpoint is disconnected or removed from the network.
An exception action is configured–If you have an exception action configured per profile that leads to an unusual or unacceptable event from that endpoint. The profiling service moves the endpoint to the corresponding static profile by issuing a CoA.
An endpoint is profiled for the first time–When an endpoint is not statically assigned and profiled for the first time; for example, the profile changes from an unknown to a known profile.+ An endpoint identity group has changed–When an endpoint is added or removed from an endpoint identity group that is used by an authorization policy.
The profiling service issues a CoA when there is any change in an endpoint identity group, and the endpoint identity group is used in the authorization policy for the following:
Question 2:
Which Cisco platform onboards the endpoint and can issue a CA-signed certificate while also automatically configuring endpoint network settings to use the signed endpoint certificate, allowing the endpoint to gain network access?
A. Cisco ISE
B. Cisco NAC
C. Cisco TACACS+
D. Cisco WSA
Correct Answer: A
Question 3:
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
A. accounting
B. assurance
C. automation
D. authentication
E. encryption
Correct Answer: BC
Question 4:
Which Cisco security solution determines if an endpoint has the latest OS updates and patches installed on the system?
A. Cisco Endpoint Security Analytics
B. Cisco AMP for Endpoints
C. Endpoint Compliance Scanner
D. Security Posture Assessment Service
Correct Answer: D
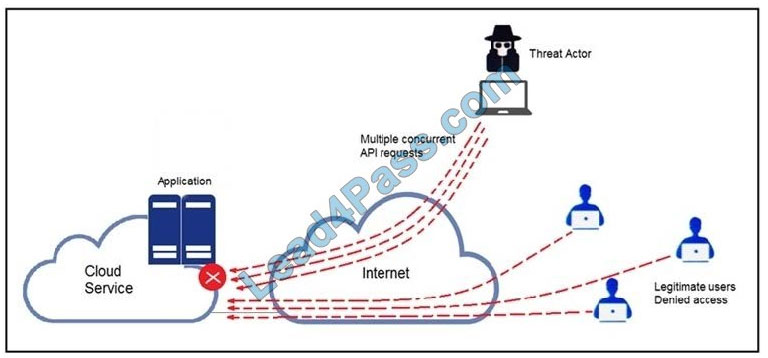
Question 5:
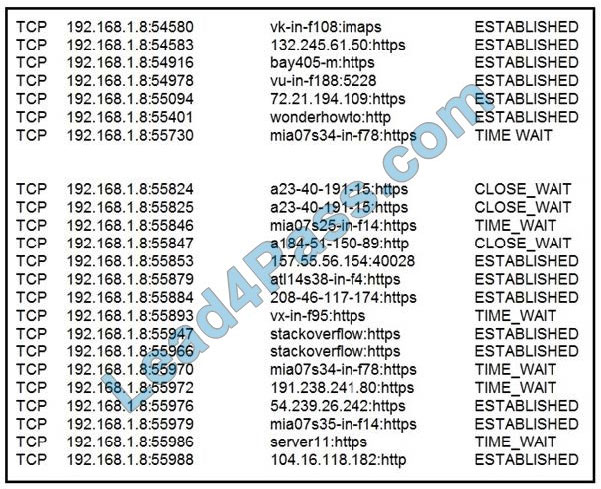
Refer to the exhibit.

What does the API key do while working with https://api.amp.cisco.com/v1/computers?
A. displays client ID
B. HTTP authorization
C. Imports requests
D. HTTP authentication
Correct Answer: D
Question 6:
What is the function of the Context Directory Agent?
A. maintains users\’ group memberships
B. relays user authentication requests from Web Security Appliance to Active Directory
C. reads the Active Directory logs to map IP addresses to usernames
D. accepts user authentication requests on behalf of Web Security Appliance for user identification
Correct Answer: C
Reference:
Question 7:
An engineer is configuring web filtering for a network using Cisco Umbrella Secure Internet Gateway.
The requirement is that all traffic needs to be filtered. Using the SSL decryption feature, which type of certificate should be presented to the end user to accomplish this goal?
A. third-party
B. self-signed
C. organization owned root
D. SubCA
Correct Answer: C
Question 8:
A network security engineer must export packet captures from the Cisco FMC web browser while troubleshooting an issue. When navigating to the address https:///capure/CAPI/pcap/test.pcap, an error 403: Forbidden is given instead of the PCAP file. Which action must the engineer take to resolve this issue?
A. Disable the proxy setting on the browser
B. Disable the HTTPS server and use HTTP instead
C. Use the Cisco FTD IP address as the proxy server setting on the browser
D. Enable the HTTPS server for the device platform policy
Correct Answer: D
Question 9:
An organization must add new firewalls to its infrastructure and wants to use Cisco ASA or Cisco FTD.
The chosen firewalls must provide methods of blocking traffic that includes offering the user the option to bypass the block for certain sites after displaying a warning page and resetting the connection.
Which solution should the organization choose?
A. Cisco FTD because it supports system rate level traffic blocking, whereas Cisco ASA does not
B. Cisco ASA because it allows for interactive blocking and blocking with reset to be configured via the GUI, whereas Cisco FTD does not.
C. Cisco FTD because it enables interactive blocking and blocking with reset natively, whereas Cisco ASA does not
D. Cisco ASA because it has an additional module that can be installed to provide multiple blocking capabilities, whereas Cisco FTD does not.
Correct Answer: C
Question 10:
Which security solution is used for posture assessment of the endpoints in a BYOD solution?
A. Cisco FTD
B. Cisco ASA
C. Cisco Umbrella
D. Cisco ISE
Correct Answer: D
Question 11:
An engineer is deploying Cisco Advanced Malware Protection (AMP) for Endpoints and wants to create a policy that prevents users from executing a file named abc424952615.exe without quarantining that file.
What type of Outbreak Control list must the SHA.-256 hash value for the file be added to in order to accomplish this?
A. Advanced Custom Detection
B. Blocked Application
C. Isolation
D. Simple Custom Detection
Correct Answer: B
Question 12:
A company recently discovered an attack propagating throughout their Windows network via a file named abc428565580xyz exe The malicious file was uploaded to a Simple Custom Detection list in the AMP for Endpoints Portal and the currently applied policy for the Windows clients was updated to reference the detection list Verification testing scans on known infected systems shows that AMP for Endpoints is not detecting the presence of this file as an indicator of compromise.
What must be performed to ensure the detection of the malicious file?
A. Upload the malicious file to the Blocked Application Control List
B. Use an Advanced Custom Detection List instead of a Simple Custom Detection List
C. Check the box in the policy configuration to send the file to Cisco Threat Grid for dynamic analysis
D. Upload the SHA-256 hash for the file to the Simple Custom Detection List
Correct Answer: D
Question 13:
Which Cisco platform provides an agentless solution to provide visibility across the network including encrypted traffic analytics to detect malware in encrypted traffic without the need for decryption?
A. Cisco Advanced Malware Protection
B. Cisco Stealthwatch
C. Cisco Identity Services Engine
D. Cisco AnyConnect
Correct Answer: B
Question 14:
Which security solution protects users leveraging DNS-layer security?
A. Cisco ISE
B. Cisco FTD
C. Cisco Umbrella
D. Cisco ASA
Correct Answer: C
Question 15:
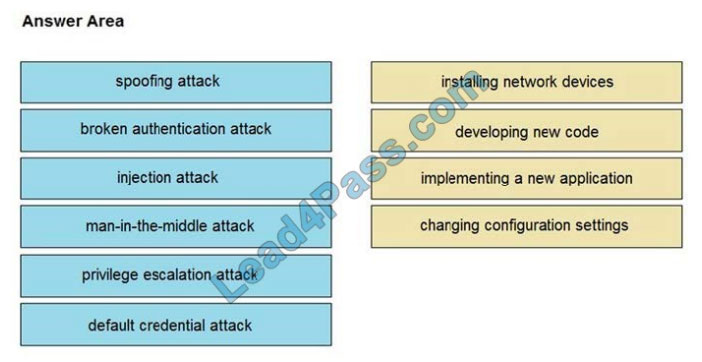
What are two ways that the Cisco Container Platform provides value to customers who utilize cloud service providers? (Choose two.)
A. Allows developers to create code once and deploy it to multiple clouds
B. helps maintain source code for cloud deployments
C. manages Docker containers
D. manages Kubernetes clusters
E. Creates complex tasks for managing code
Correct Answer: AE
…
leads4pass 350-701 dumps contain 598 latest exam questions and answers, reviewed by the Cisco professional team to ensure authenticity and effectiveness, welcome to use 350-701 SCOR dumps: https://www.leads4pass.com/350-701.html to ensure Implementing and Operating The Cisco Security Core Technologies (SCOR) certification exam was successfully passed on the first try.