How to pass Cisco CCNP Security 300-209 dumps exam? High quality Cisco CCNP Security 300-209 dumps pdf training resources and study guides free download from lead4pass. The best useful Cisco CCNP Security 300-209 dumps pdf files and vce youtube demo update free shared. “Implementing Cisco Secure Mobility Solutions” is the name of Cisco CCNP Security https://www.leads4pass.com/300-209.html exam dumps which covers all the knowledge points of the real Cisco CCNP Security. Latest Cisco CCNP Security 300-209 dumps exam practice questions and answers free download, pass Cisco 300-209 exam test quickly and easily at first try.
High quality Cisco 300-209 dumps pdf training resource: https://drive.google.com/open?id=0B_7qiYkH83VROWtCY2Nqc1Yta2c
High quality Cisco 300-208 dumps pdf training resource: https://drive.google.com/open?id=0B_7qiYkH83VRWWVtSWlTWENZMzA
Latest Cisco CCNP Security 300-209 Dumps Exam Questions And Answers (1-30)
QUESTION 1
An administrator wishes to limit the networks reachable over the Anyconnect VPN tunnels. Which configuration on the ASA will correctly limit the networks reachable to 209.165.201.0/27 and 209.165.202.128/27?
A. access-list splitlist standard permit 209.165.201.0 255.255.255.224 access-list splitlist standard permit 209.165.202.128 255.255.255.224 ! group-policy GroupPolicy1 internal group-policy GroupPolicy1 attributes split-tunnelpolicy tunnelspecified split-tunnel-network-list value splitlist
B. access-list splitlist standard permit 209.165.201.0 255.255.255.224 access-list splitlist standard permit 209.165.202.128 255.255.255.224 ! group-policy GroupPolicy1 internal group-policy GroupPolicy1 attributes split-tunnelpolicy tunnelall split tunnel-network-list value splitlist
C. group-policy GroupPolicy1 internal group-policy GroupPolicy1 attributes split-tunnel-policy tunnelspecified split tunnelnetwork-list ipv4 1 209.165.201.0 255.255.255.224 split-tunnel-network-list ipv4 2 209.165.202.128 255.255.255.224
D. access-list splitlist standard permit 209.165.201.0 255.255.255.224 access-list splitlist standard permit 209.165.202.128 255.255.255.224 ! crypto anyconnect vpn-tunnel-policy tunnelspecified crypto anyconnect vpn-tunnelnetwork-list splitlist
E. crypto anyconnect vpn-tunnel-policy tunnelspecified crypto anyconnect split-tunnel-network-list ipv4 1 209.165.201.0 255.255.255.224 crypto anyconnect split-tunnel-network-list ipv4 2 209.165.202.128 255.255.255.224
Correct Answer: A
QUESTION 2
Which two RADIUS attributes are needed for a VRF-aware FlexVPN hub? (Choose two.)
A. ip:interface-config=ip unnumbered loobackn
B. ip:interface-config=ip vrf forwarding ivrf
C. ip:interface-config=ip src route
D. ip:interface-config=ip next hop
E. ip:interface-config=ip neighbor 0.0.0.0
Correct Answer: AB
QUESTION 3
What is the default storage location of user-level bookmarks in an IOS clientless SSL VPN?
A. disk0:/webvpn/{context name}/
B. disk1:/webvpn/{context name}/
C. flash:/webvpn/{context name}/
D. nvram:/webvpn/{context name}/
Correct Answer: C
QUESTION 4
Which three configurations are prerequisites for stateful failover for IPsec? (Choose three.)
A. Only the IKE configuration that is set up on the active device must be duplicated on the standby device; the IPsec configuration is copied automatically.
B. Only crypto map configuration that is set up on the active device must be duplicated on the standby device.
C. The IPsec configuration that is set up on the active device must be duplicated on the standby device.
D. The active and standby devices can run different versions of the Cisco IOS software but need to be the same type of device.
E. The active and standby devices must run the same version of the Cisco IOS software and should be the same type of device.
F. Only the IPsec configuration that is set up on the active device must be duplicated on the standby device; the IKE configuration is copied automatically.
G. The IKE configuration that is set up on the active device must be duplicated on the standby device.
Correct Answer: CEG
QUESTION 5
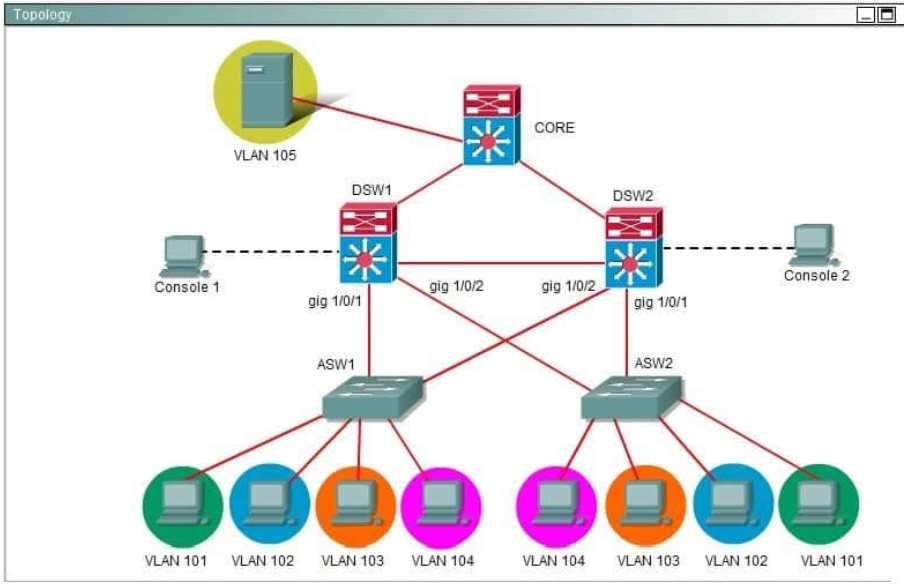
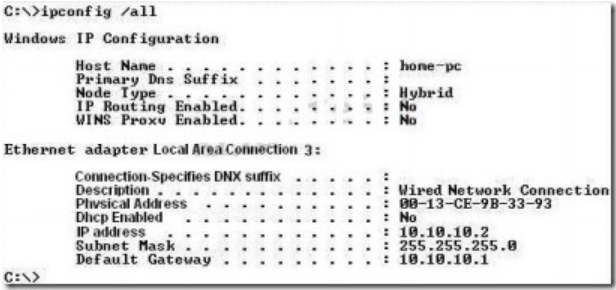
Refer to the exhibit.
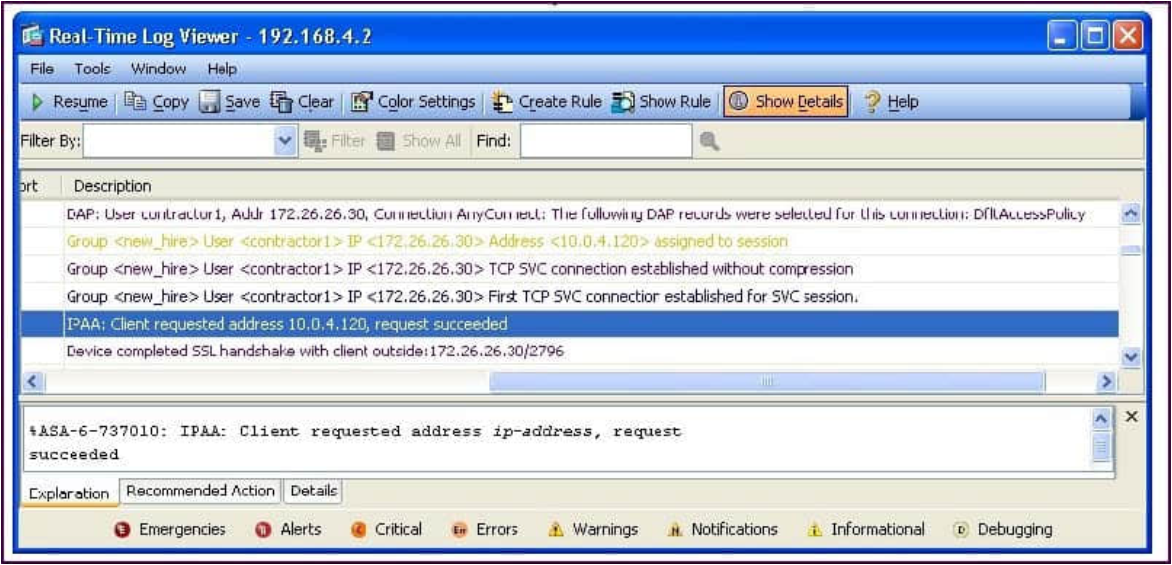
A new NOC engineer, while viewing a real-time log from an SSL VPN tunnel, has a question a line in the log.
The IP address 172.26.26.30 is attached to which interface in the network? 300-209 dumps
A. the Cisco ASA physical interface
B. the physical interface of the end user
C. the Cisco ASA SSL VPN tunnel interface
D. the SSL VPN tunnel interface of the end user
Correct Answer: B
QUESTION 6
Which cryptographic algorithms are a part of the Cisco NGE suite?
A. HIPPA DES
B. AES-CBC-128
C. RC4-128
D. AES-GCM-256
Correct Answer: D
QUESTION 7
Which two qualify as Next Generation Encryption integrity algorithms? (Choose two.)
A. SHA-512
B. SHA-256
C. SHA-192
D. SHA-380
E. SHA-192
F. SHA-196
Correct Answer: AB
QUESTION 8
Which command specifies the path to the Host Scan package in an ASA AnyConnect VPN?
A. csd hostscan path image
B. csd hostscan image path
C. csd hostscan path
D. hostscan image path
Correct Answer: B
QUESTION 9
Which transform set is contained in the IKEv2 default proposal?
A. aes-cbc-192, sha256, group 14
B. 3des, md5, group 7
C. 3des, sha1, group 1
D. aes-cbc-128, sha, group 5
Correct Answer: D
QUESTION 10
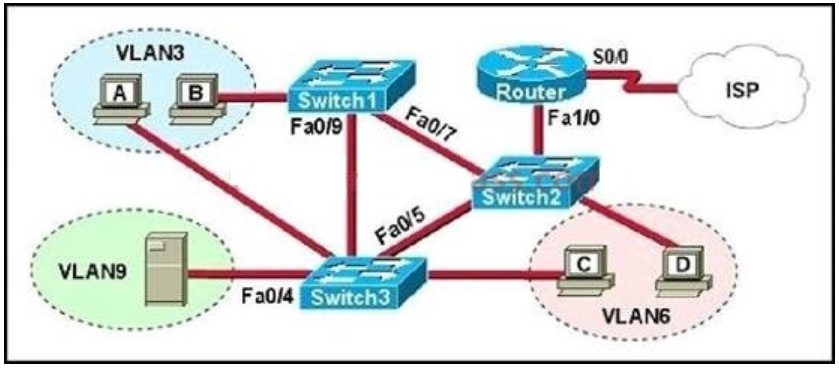
Refer to the exhibit.
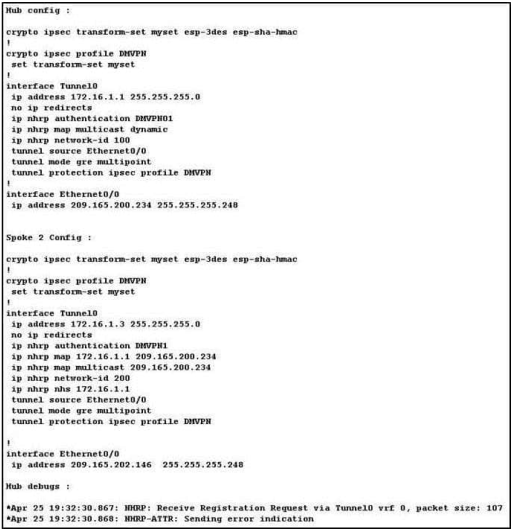
The network administrator is adding a new spoke, but the tunnel is not passing traffic. What could cause this issue?
A. DMVPN is a point-to-point tunnel, so there can be only one spoke.
B. There is no EIGRP configuration, and therefore the second tunnel is not working.
C. The NHRP authentication is failing.
D. The transform set must be in transport mode, which is a requirement for DMVPN.
E. The NHRP network ID is incorrect.
Correct Answer: C
QUESTION 11
An XYZ Corporation systems engineer, while making a sales call on the ABC Corporation headquarters, tried to access the XYZ sales demonstration folder to transfer a demonstration via FTP from an ABC conference room behind the firewall. The engineer could not reach XYZ through the remote-access VPN tunnel. From home the previous day, however, the engineer did connect to the XYZ sales demonstration folder and transferred the demonstration via IPsec over DSL.
To get the connection to work and transfer the demonstration, what should the engineer do?
A. Change the MTU size on the IPsec client to account for the change from DSL to cable transmission.
B. Enable the local LAN access option on the IPsec client.
C. Enable the IPsec over TCP option on the IPsec client.
D. Enable the clientless SSL VPN option on the PC.
Correct Answer: C
QUESTION 12
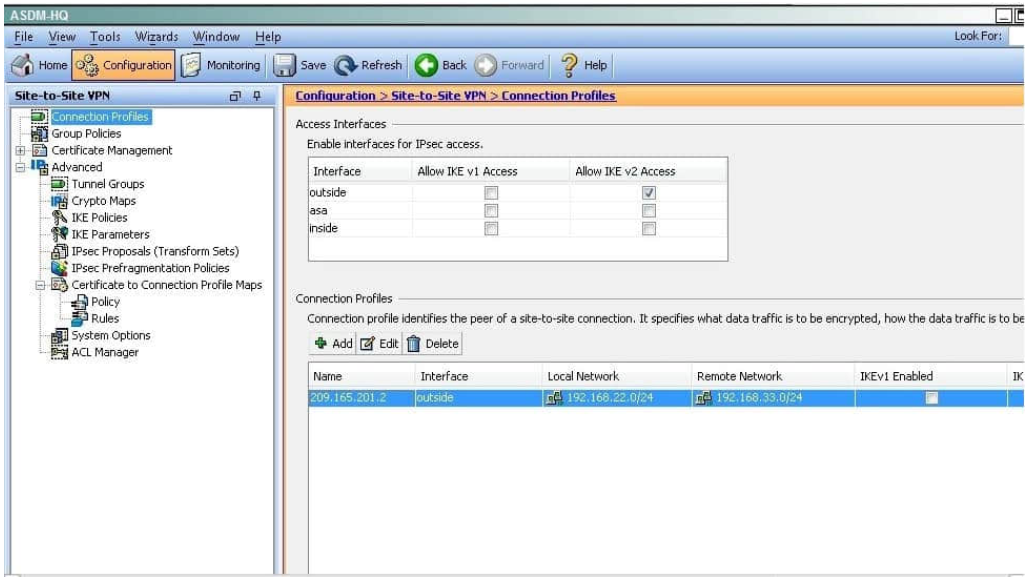
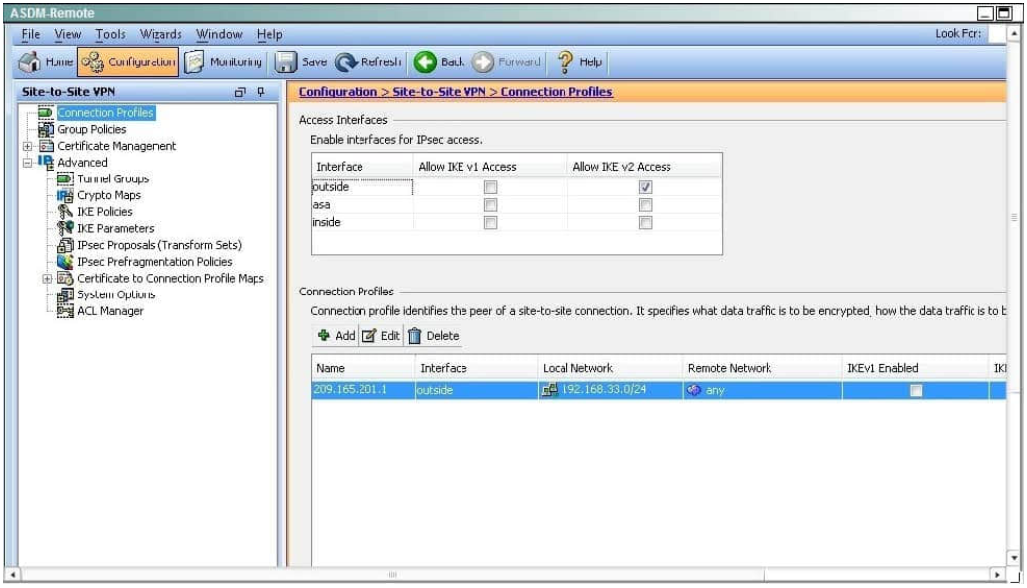
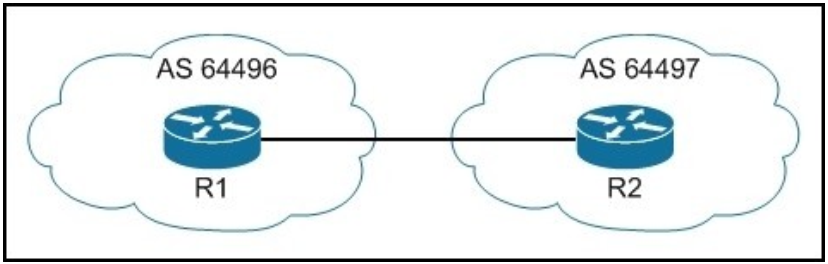
When a tunnel is initiated by the headquarter ASA, which one of the following Diffie- Hellman groups is selected by the headquarter ASA during CREATE_CHILD_SA exchange?
A. 1
B. 2
C. 5
D. 14
E. 19
Correct Answer: C
QUESTION 13
Which two troubleshooting steps should be taken when Cisco AnyConnect cannot establish an IKEv2 connection, while SSL works fine? 300-209 dumps (Choose two.)
A. Verify that the primary protocol on the client machine is set to IPsec.
B. Verify that AnyConnect is enabled on the correct interface.
C. Verify that the IKEv2 protocol is enabled on the group policy.
D. Verify that ASDM and AnyConnect are not using the same port.
E. Verify that SSL and IKEv2 certificates are not referencing the same trustpoint.
Correct Answer: AC
QUESTION 14
When you troubleshoot Cisco AnyConnect, which step does Cisco recommend before you open a TAC case?
A. Show applet Lifecycle exceptions.
B. Disable cookies.
C. Enable the WebVPN cache.
D. Collect a DART bundle.
Correct Answer: D
QUESTION 15
Refer to the exhibit.
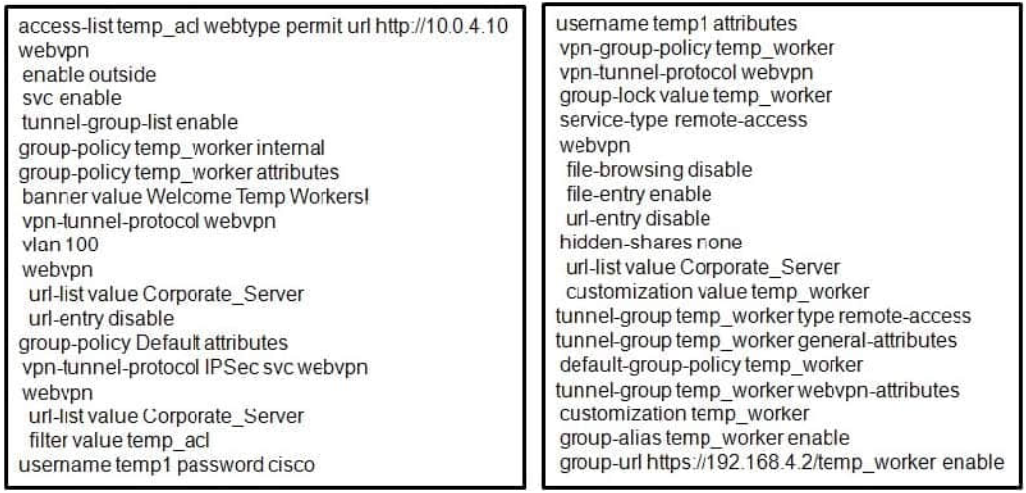
A junior network engineer configured the corporate Cisco ASA appliance to accommodate a new temporary worker. For security reasons, the IT department wants to restrict the internal network access of the new temporary worker to the corporate server, with an IP address of 10.0.4.10. After the junior network engineer finished the configuration, an IT security specialist tested the account of the temporary worker. The tester was able to access the URLs of additional secure servers from the WebVPN user account of the temporary worker.
What did the junior network engineer configure incorrectly?
A. The ACL was configured incorrectly.
B. The ACL was applied incorrectly or was not applied.
C. Network browsing was not restricted on the temporary worker group policy.
D. Network browsing was not restricted on the temporary worker user policy.
Correct Answer: B
QUESTION 16
Which DAP endpoint attribute checks for the matching MAC address of a client machine?
A. device
B. process
C. antispyware
D. BIA
Correct Answer: A
QUESTION 17
In the Cisco ASDM interface, where do you enable the DTLS protocol setting?
A. Configuration andgt; Remote Access VPN andgt; Network (Client) Access andgt; Group Policies andgt; Add or Edit andgt; Add or Edit Internal Group Policy
B. Configuration andgt; Remote Access VPN andgt; Network (Client) Access andgt; AAA Setup andgt; Local Users andgt; Add or Edit
C. Device Management andgt; Users/AAA andgt; User Accounts andgt; Add or Edit andgt; Add or Edit User Account andgt; VPN Policy andgt; SSL VPN Client
D. Configuration andgt; Remote Access VPN andgt; Network (Client) Access andgt; Group Policies andgt; Add or Edit
Correct Answer: C
QUESTION 18
Which command enables IOS SSL VPN Smart Tunnel support for PuTTY?
A. appl ssh putty.exe win
B. appl ssh putty.exe windows
C. appl ssh putty
D. appl ssh putty.exe
Correct Answer: B
QUESTION 19
Refer to the exhibit.
![]()
While troubleshooting a remote-access application, a new NOC engineer received the logging message that is shown in the exhibit. Which configuration is most likely to be mismatched?
A. IKE configuration
B. extended authentication configuration
C. IPsec configuration
D. digital certificate configuration
Correct Answer: C
QUESTION 20
You have deployed new Cisco AnyConnect start before logon modules and set the configuration to download modules before logon, but all client connections continue to use the previous version of the module.
Which action must you take to correct the problem?
A. Configure start before logon in the client profile.
B. Configure a group policy to prompt the user to download the updated module.
C. Define the modules for download in the client profile.
D. Define the modules for download in the group policy.
Correct Answer: A
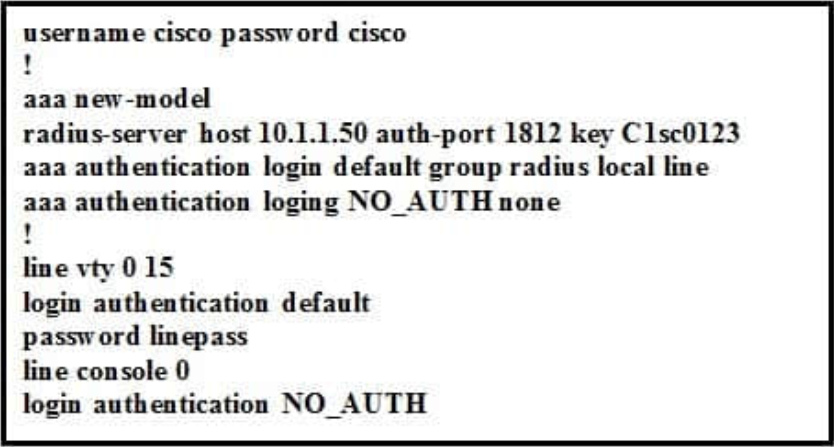
QUESTION 21
Refer to the exhibit.
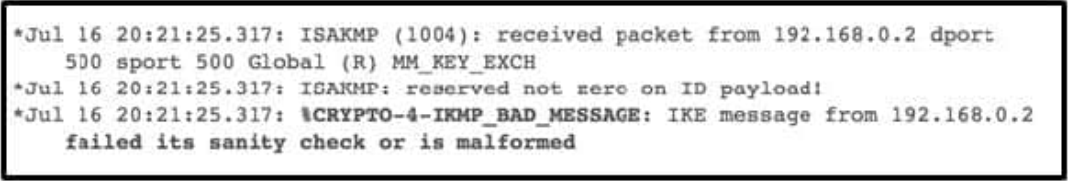
Which type of mismatch is causing the problem with the IPsec VPN tunnel?
A. PSK
B. Phase 1 policy
C. transform set
D. crypto access list
Correct Answer: A
QUESTION 22
Which two are features of GETVPN but not DMVPN and FlexVPN? (Choose two.)
A. one IPsec SA for all encrypted traffic
B. no requirement for an overlay routing protocol
C. design for use over public or private WAN
D. sequence numbers that enable scalable replay checking
E. enabled use of ESP or AH
F. preservation of IP protocol in outer header
Correct Answer: AB
QUESTION 23
A spoke has two Internet connections for failover. How can you achieve optimum failover without affecting any other router in the DMVPN cloud? 300-209 dumps
A. Create another DMVPN cloud by configuring another tunnel interface that is sourced from the second ISP link.
B. Use another router at the spoke site, because two ISP connections on the same router for the same hub is not allowed.
C. Configure SLA tracking, and when the primary interface goes down, manually change the tunnel source of the tunnel interface.
D. Create another tunnel interface with same configuration except the tunnel source, and configure the if-state nhrp and backup interface commands on the primary tunnel interface.
Correct Answer: C
QUESTION 24
Refer to the exhibit.
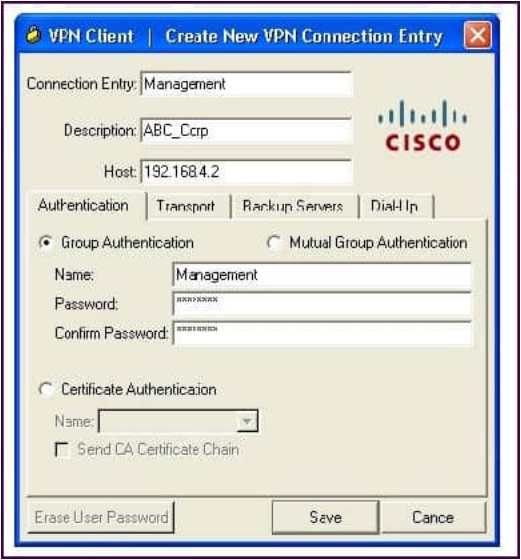
A NOC engineer is in the process of entering information into the Create New VPN Connection Entry fields.
Which statement correctly describes how to do this?
A. In the Connection Entry field, enter the name of the connection profile as it is specified on the Cisco ASA appliance.
B. In the Host field, enter the IP address of the remote client device.
C. In the Authentication tab, click the Group Authentication or Mutual Group Authentication radio button to enable symmetrical pre-shared key authentication.
D. In the Name field, enter the name of the connection profile as it is specified on the Cisco ASA appliance.
Correct Answer: D
QUESTION 25
Refer to the exhibit.
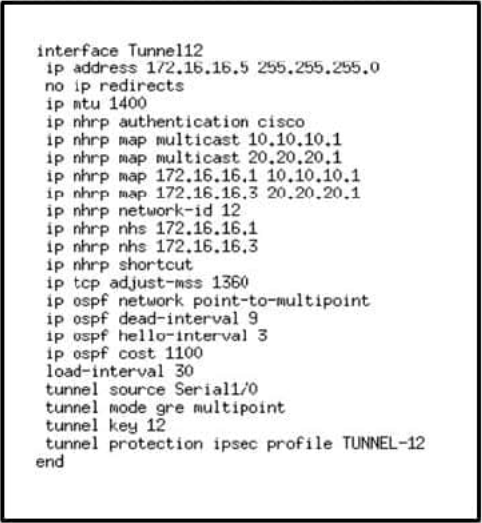
Which two characteristics of the VPN implementation are evident? (Choose two.)
A. dual DMVPN cloud setup with dual hub
B. DMVPN Phase 3 implementation
C. single DMVPN cloud setup with dual hub
D. DMVPN Phase 1 implementation
E. quad DMVPN cloud with quadra hub
F. DMVPN Phase 2 implementation
Correct Answer: BC
QUESTION 26
Which two statements comparing ECC and RSA are true? (Choose two.)
A. ECC can have the same security as RSA but with a shorter key size.
B. ECC lags in performance when compared with RSA.
C. Key generation in ECC is slower and less CPU intensive.
D. ECC cannot have the same security as RSA, even with an increased key size.
E. Key generation in ECC is faster and less CPU intensive.
Correct Answer: AE
QUESTION 27
An administrator desires that when work laptops are not connected to the corporate network, they should automatically initiate an AnyConnect VPN tunnel back to headquarters. Where does the administrator configure this?
A. Via the svc trusted-network command under the group-policy sub-configuration mode on the ASA
B. Under the andquot;Automatic VPN Policyandquot; section inside the Anyconnect Profile Editor within ASDM
C. Under the TNDPolicy XML section within the Local Preferences file on the client computer
D. Via the svc trusted-network command under the global webvpn sub-configuration mode on the ASA
Correct Answer: C
QUESTION 28
Which command simplifies the task of converting an SSL VPN to an IKEv2 VPN on a Cisco ASA appliance that has an invalid IKEv2 configuration?
A. migrate remote-access ssl overwrite
B. migrate remote-access ikev2
C. migrate l2l
D. migrate remote-access ssl
Correct Answer: A
QUESTION 29
Which three types of web resources or protocols are enabled by default on the Cisco ASA Clientless SSL VPN portal? (Choose three.)
A. HTTP
B. VNC
C. CIFS
D. RDP
E. HTTPS
F. ICA (Citrix)
Correct Answer: ACE
QUESTION 30
Which functionality is provided by L2TPv3 over FlexVPN? 300-209 dumps
A. the extension of a Layer 2 domain across the FlexVPN
B. the extension of a Layer 3 domain across the FlexVPN
C. secure communication between servers on the FlexVPN
D. a secure backdoor for remote access users through the FlexVPN
Correct Answer: A
What Our Customers Are Saying:
Newest helpful Cisco CCNP Security 300-209 dumps exam practice materials in PDF format free download from lead4pass. The best and most updated latest Cisco CCNP Security https://www.leads4pass.com/300-209.html dumps pdf training resources which are the best for clearing 300-209 exam test, and to get certified by Cisco CCNP Security, download one of the many PDF readers that are available for free, 100% pass guarantee.
Best Cisco CCNP Security 300-209 dumps vce youtube: https://youtu.be/HyFmJ304YRE
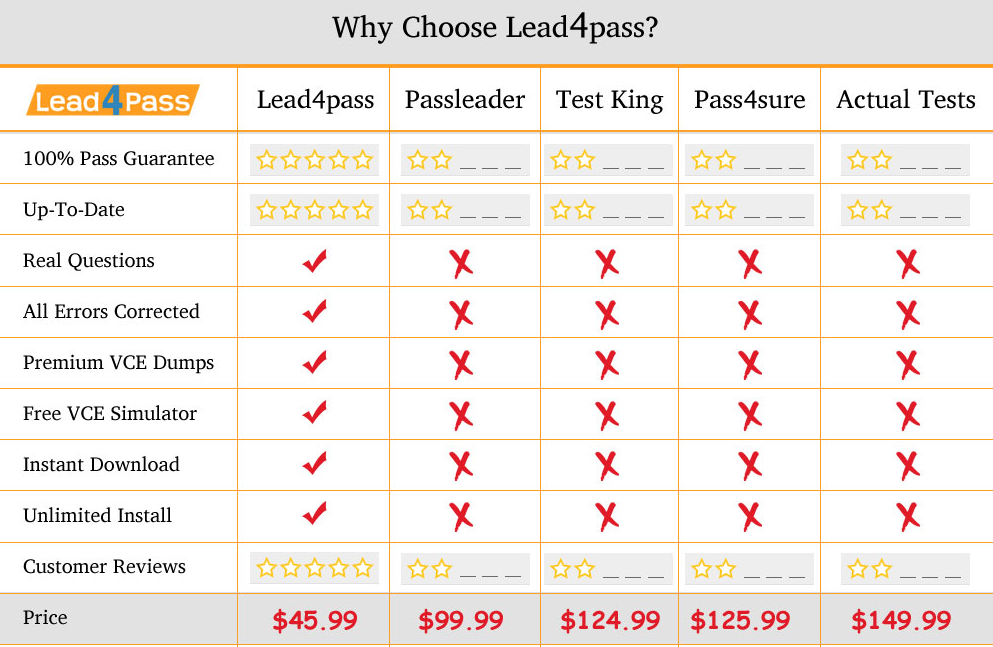
Why Choose Lead4pass?
Lead4pass is the best provider of IT learning materials and the right choice for you to pass the exam. Other brands started earlier, but the questions are not the newest the price is relatively expensive. Lead4pass provide the latest real and cheapest questions and answers, help you pass the exam easily at first try.